We design Mac hardware and software with advanced technologies that work together to run apps more securely, protect your data, and help keep you safe on the web. And with macOS Big Sur available as a free upgrade, it’s easy to get the most secure version of macOS for your Mac.*

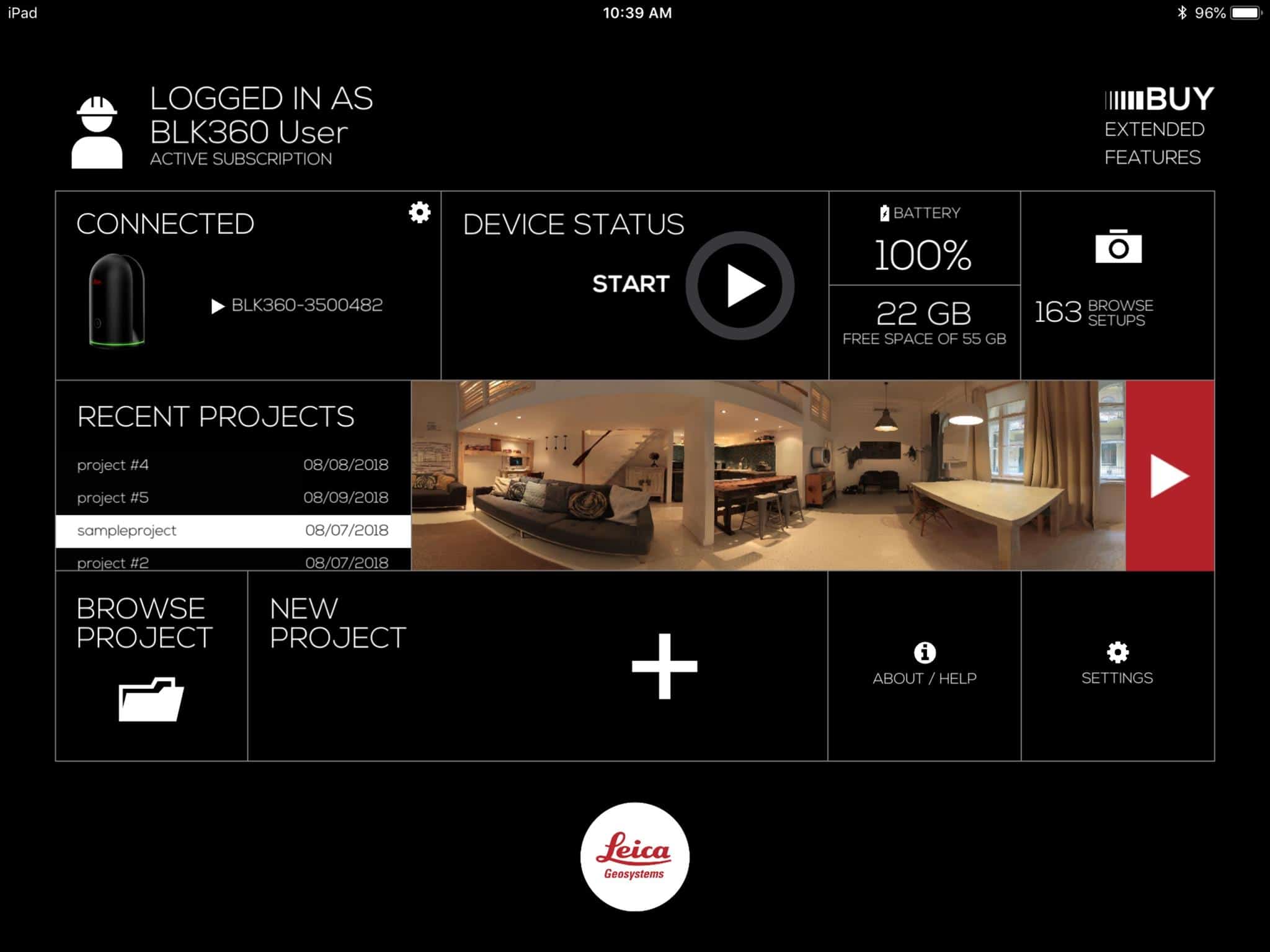
Improve your workflows and save both time and money with the revolutionary Leica BLK360 Imaging Laser Scanner. Package includes: Leica BLK360 Imaging Laser Scanner; 2 x GEB212 Lithium-Ion Battery for the BLK360; GKL311 Battery; Charger and AC/DC Adapter; Leica BLK360 Tripod; Leica BLK360 Mission Bag; 2 Year Warranty. Our BitTorrent Web and Classic clients for Mac computers are available in one convenient location. Download the version that best suits you. When the Arduino Software (IDE) is properly installed you can go back to the Getting Started Home and choose your board from the list on the right of the page. Last revision 2016/08/09 by SM. The text of the Arduino getting started guide is licensed under a Creative Commons Attribution-ShareAlike 3.0 License. Code samples in the guide are.
Apple M1 chip.
A shared architecture for security.
The Apple M1 chip with built-in Secure Enclave brings the same powerful security capabilities of iPhone to Mac — protecting your login password, automatically encrypting your data, and powering file-level encryption so you stay safe. And the Apple M1 chip keeps macOS secure while it’s running, just as iOS has protected iPhone for years.
Apple helps you keep your Mac secure with software updates.The best way to keep your Mac secure is to run the latest software. When new updates are available, macOS sends you a notification — or you can opt in to have updates installed automatically when your Mac is not in use. macOS checks for new updates every day and starts applying them in the background, so it’s easier and faster than ever to always have the latest and safest version.

The technically sophisticated runtime protections in macOS work at the very core of your Mac to keep your system safe from malware. This starts with state-of-the-art antivirus software built in to block and remove malware. Technologies like XD (execute disable), ASLR (address space layout randomization), and SIP (system integrity protection) make it difficult for malware to do harm, and they ensure that processes with root permission cannot change critical system files.
Download apps safely from the Mac App Store. And the internet.Now apps from both the App Store and the internet can be installed worry-free. App Review makes sure each app in the App Store is reviewed before it’s accepted. Gatekeeper on your Mac ensures that all apps from the internet have already been checked by Apple for known malicious code — before you run them the first time. If there’s ever a problem with an app, Apple can quickly stop new installations and even block the app from launching again.
Stay in control of what data apps can access.Apps need your permission to access files in your Documents, Downloads, and Desktop folders as well as in iCloud Drive and external volumes. And you’ll be prompted before any app can access the camera or mic, capture keyboard activity, or take a photo or video of your screen.
FileVault 2 encrypts your data.With FileVault 2, your data is safe and secure — even if your Mac falls into the wrong hands. FileVault 2 encrypts the entire drive on your Mac, protecting your data with XTS-AES 128 encryption. Mac computers built on the Apple M1 chip take data protection even further by using dedicated hardware to protect your login password and enabling file-level encryption, which developers can take advantage of — just as on iPhone.
Designed to protect your privacy.Online privacy isn’t just something you should hope for — it’s something you should expect. That’s why Safari comes with powerful privacy protection technology built in, including Intelligent Tracking Prevention that identifies trackers and helps prevent them from profiling or following you across the web. A new weekly Privacy Report on your start page shows how Safari protects you as you browse over time. Or click the Privacy Report button in your Safari toolbar for an instant snapshot of the cross-site trackers Safari is actively preventing on that web page.
Automatic protections from intruders.Safari uses iCloud Keychain to securely store your passwords across all your devices. If it ever detects a security concern, Password Monitoring will alert you. Safari also prevents suspicious websites from loading and warns you if they’re detected. And because it runs web pages in separate processes, any harmful code is confined to a single browser tab and can’t crash the whole browser or access your data.
Find your missing Mac with Find My. Blk360 Program For Mac ComputersThe Find My app can help you locate a missing Mac — even if it’s offline or sleeping — by sending out Bluetooth signals that can be detected by nearby Apple devices. These devices then relay the detected location of your Mac to iCloud so you can locate it. It’s all anonymous and encrypted end-to-end so no one — including Apple — knows the identity of any reporting device or the location of your Mac. And it all happens silently using tiny bits of data that piggyback on existing network traffic. So there’s no need to worry about your battery life, your data usage, or your privacy being compromised.
Keep your Mac safe.Even if it’s in the wrong hands.
All Mac systems built on the Apple M1 chip or with the Apple T2 Security Chip support Activation Lock, just like your iPhone or iPad. So if your Mac is ever misplaced or lost, the only person who can erase and reactivate it is you.
Windows 10/8.1/8/7/Vista/XP/Server 2012 R2/Server 2012/Server 2008 R2/Server 2008/Server 2003/Server 2000
Technitium MAC Address Changer allows you to change (spoof) Media Access Control (MAC) Address of your Network Interface Card (NIC) instantly. It has a very simple user interface and provides ample information regarding each NIC in the machine. Every NIC has a MAC address hard coded in its circuit by the manufacturer. This hard coded MAC address is used by windows drivers to access Ethernet Network (LAN). This tool can set a new MAC address to your NIC, bypassing the original hard coded MAC address. Technitium MAC Address Changer is a must tool in every security professionals tool box.
Features- Works on Windows 10, 8 & 7 for both 32-bit and 64-bit.
- Enhanced network configuration presets with IPv6 support allow you to quickly switch between network configurations.
- Allows complete configuration of any network adapter.
- Command line options with entire software functionality available. You can select a preset from specified preset file to apply directly.
- Update network card vendors list feature allows you to download latest vendor data (OUI) from IEEE.org.
This software just writes a value into the windows registry. When the Network Adapter Device is enabled, windows searches for the registry value 'NetworkAddress' in the key HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlClass{4D36E972-E325-11CE-BFC1- 08002bE10318}[ID of NIC e.g. 0001]. If a value is present, windows will use it as MAC address, if not, windows will use the hard coded manufacturer provided MAC address. Some Network Adapter drivers have this facility built-in. It can be found in the Advance settings tab in the Network Adapter's Device properties in Windows Device Manager.
Blk360 Program For Mac Catalina How To Change MAC Address- Starting MAC address changer will list all available network adapters.
- Select the adapter you want to change the MAC address. You will get the details of your selection below.
- In the Information tab, find the Change MAC Address frame. Enter new MAC address in the field and click Change Now! button. You may even click Random MAC Address button to fill up a randomly selected MAC address from the vendor list available.
- To restore the original MAC address of the network adapter, select the adapter, click Restore Original button in the Change MAC Address frame.

Improve your workflows and save both time and money with the revolutionary Leica BLK360 Imaging Laser Scanner. Package includes: Leica BLK360 Imaging Laser Scanner; 2 x GEB212 Lithium-Ion Battery for the BLK360; GKL311 Battery; Charger and AC/DC Adapter; Leica BLK360 Tripod; Leica BLK360 Mission Bag; 2 Year Warranty. Our BitTorrent Web and Classic clients for Mac computers are available in one convenient location. Download the version that best suits you. When the Arduino Software (IDE) is properly installed you can go back to the Getting Started Home and choose your board from the list on the right of the page. Last revision 2016/08/09 by SM. The text of the Arduino getting started guide is licensed under a Creative Commons Attribution-ShareAlike 3.0 License. Code samples in the guide are.
Apple M1 chip.
A shared architecture for security.
The Apple M1 chip with built-in Secure Enclave brings the same powerful security capabilities of iPhone to Mac — protecting your login password, automatically encrypting your data, and powering file-level encryption so you stay safe. And the Apple M1 chip keeps macOS secure while it’s running, just as iOS has protected iPhone for years.
Apple helps you keep your Mac secure with software updates.The best way to keep your Mac secure is to run the latest software. When new updates are available, macOS sends you a notification — or you can opt in to have updates installed automatically when your Mac is not in use. macOS checks for new updates every day and starts applying them in the background, so it’s easier and faster than ever to always have the latest and safest version.
Protection starts at the core.The technically sophisticated runtime protections in macOS work at the very core of your Mac to keep your system safe from malware. This starts with state-of-the-art antivirus software built in to block and remove malware. Technologies like XD (execute disable), ASLR (address space layout randomization), and SIP (system integrity protection) make it difficult for malware to do harm, and they ensure that processes with root permission cannot change critical system files.
Download apps safely from the Mac App Store. And the internet.Now apps from both the App Store and the internet can be installed worry-free. App Review makes sure each app in the App Store is reviewed before it’s accepted. Gatekeeper on your Mac ensures that all apps from the internet have already been checked by Apple for known malicious code — before you run them the first time. If there’s ever a problem with an app, Apple can quickly stop new installations and even block the app from launching again.
Stay in control of what data apps can access.Apps need your permission to access files in your Documents, Downloads, and Desktop folders as well as in iCloud Drive and external volumes. And you’ll be prompted before any app can access the camera or mic, capture keyboard activity, or take a photo or video of your screen.
FileVault 2 encrypts your data.With FileVault 2, your data is safe and secure — even if your Mac falls into the wrong hands. FileVault 2 encrypts the entire drive on your Mac, protecting your data with XTS-AES 128 encryption. Mac computers built on the Apple M1 chip take data protection even further by using dedicated hardware to protect your login password and enabling file-level encryption, which developers can take advantage of — just as on iPhone.
Designed to protect your privacy.Online privacy isn’t just something you should hope for — it’s something you should expect. That’s why Safari comes with powerful privacy protection technology built in, including Intelligent Tracking Prevention that identifies trackers and helps prevent them from profiling or following you across the web. A new weekly Privacy Report on your start page shows how Safari protects you as you browse over time. Or click the Privacy Report button in your Safari toolbar for an instant snapshot of the cross-site trackers Safari is actively preventing on that web page.
Automatic protections from intruders.Safari uses iCloud Keychain to securely store your passwords across all your devices. If it ever detects a security concern, Password Monitoring will alert you. Safari also prevents suspicious websites from loading and warns you if they’re detected. And because it runs web pages in separate processes, any harmful code is confined to a single browser tab and can’t crash the whole browser or access your data.
Find your missing Mac with Find My. Blk360 Program For Mac ComputersThe Find My app can help you locate a missing Mac — even if it’s offline or sleeping — by sending out Bluetooth signals that can be detected by nearby Apple devices. These devices then relay the detected location of your Mac to iCloud so you can locate it. It’s all anonymous and encrypted end-to-end so no one — including Apple — knows the identity of any reporting device or the location of your Mac. And it all happens silently using tiny bits of data that piggyback on existing network traffic. So there’s no need to worry about your battery life, your data usage, or your privacy being compromised.
Keep your Mac safe.Even if it’s in the wrong hands.
All Mac systems built on the Apple M1 chip or with the Apple T2 Security Chip support Activation Lock, just like your iPhone or iPad. So if your Mac is ever misplaced or lost, the only person who can erase and reactivate it is you.
Windows 10/8.1/8/7/Vista/XP/Server 2012 R2/Server 2012/Server 2008 R2/Server 2008/Server 2003/Server 2000
Technitium MAC Address Changer allows you to change (spoof) Media Access Control (MAC) Address of your Network Interface Card (NIC) instantly. It has a very simple user interface and provides ample information regarding each NIC in the machine. Every NIC has a MAC address hard coded in its circuit by the manufacturer. This hard coded MAC address is used by windows drivers to access Ethernet Network (LAN). This tool can set a new MAC address to your NIC, bypassing the original hard coded MAC address. Technitium MAC Address Changer is a must tool in every security professionals tool box.
Features- Works on Windows 10, 8 & 7 for both 32-bit and 64-bit.
- Enhanced network configuration presets with IPv6 support allow you to quickly switch between network configurations.
- Allows complete configuration of any network adapter.
- Command line options with entire software functionality available. You can select a preset from specified preset file to apply directly.
- Update network card vendors list feature allows you to download latest vendor data (OUI) from IEEE.org.
This software just writes a value into the windows registry. When the Network Adapter Device is enabled, windows searches for the registry value 'NetworkAddress' in the key HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlClass{4D36E972-E325-11CE-BFC1- 08002bE10318}[ID of NIC e.g. 0001]. If a value is present, windows will use it as MAC address, if not, windows will use the hard coded manufacturer provided MAC address. Some Network Adapter drivers have this facility built-in. It can be found in the Advance settings tab in the Network Adapter's Device properties in Windows Device Manager.
Blk360 Program For Mac Catalina How To Change MAC Address- Starting MAC address changer will list all available network adapters.
- Select the adapter you want to change the MAC address. You will get the details of your selection below.
- In the Information tab, find the Change MAC Address frame. Enter new MAC address in the field and click Change Now! button. You may even click Random MAC Address button to fill up a randomly selected MAC address from the vendor list available.
- To restore the original MAC address of the network adapter, select the adapter, click Restore Original button in the Change MAC Address frame.
NOTE: This tool cannot change MAC address of Microsoft Network Bridge. Network Bridge will automatically use the original MAC address of the first NIC added into bridge with the first octet of MAC address set to 0x02.
Help TopicsClick here for frequently asked help queries.
BlogRead this blog post for more details on issues with wireless networks and workaround.
